 Popular Posts
Popular PostsUnderstanding Cryptocurrency Mining Pools: Advantages and Drawbacks
A cryptocurrency mining pool is a collective of miners who consolidate their computational resources over a network to enhance the probability of receiving block rewards from mining. The rewards are s
/images/image1.png)
popular
What is a Seed Phrase and Why Is It Crucial for Cryptocurrency Wallets?
Among the key tools to secure digital assets, seed phrases play a critical role. This article aims to unravel the concept of seed phrases and their crucial role in safeguarding cryptocurrency wallets.
/images/image1.png)
popular
What is Cryptocurrency Mining Difficulty and How Is It Adjusted?
Mining, in the cryptocurrency context, is the process by which new digital currency coins are generated, and transactions are confirmed and added to the blockchain public ledger. However, mining is no
/images/image1.png)
popular
The Ultimate Guide to Blockchain Light Clients
While decentralization may be the fundamental property of blockchains, it isn't an end goal in itself. Instead, it's pursued—often at the expense of other desirable properties like scalability—for the

popular
What is a Multi-Signature (Multisig) Wallet in Cryptocurrency?
As digital currencies continue to gain traction, the need for secure transactions and storage solutions has become more pronounced than ever. One such solution that has emerged in response to this nee
/images/image1.png)
popular
What are Blockchain/Cross-Chain Bridges?
While these networks have brought about significant innovation, their fragmentation has also created siloed environments, hindering their collaboration and interoperability. Blockchain bridges, also k
/images/image1.png)
popular
What is a Cold Wallet and Why is It Important for Cryptocurrency Security?
Cryptocurrency, a form of digital or virtual currency, operates independently of a central bank and uses encryption techniques to regulate the generation of units and verify transactions. This innovat
/images/image1.png)
popular
A Primer on BFT Consensus Mechanisms in Blockchain
A blockchain is a decentralized, distributed ledger that records transactions across a multitude of computers in a manner that prevents the retroactive alteration of confirmed transactions. This techn
/images/image1.png)
popular
What is a Light Client in Blockchain Technology?
At the heart of this technology are blockchain clients, which play a crucial role in maintaining the integrity and functionality of the blockchain network. Among these clients, light clients have emer
/images/image1.png)
popular
What is a Non-Custodial Crypto Wallet?
Among these types of wallets, self-custody or non-custodial wallets stand out for their emphasis on user control and privacy. This article will delve into self-custody crypto wallets, how they work, a
/images/image1.png)
popular
A Deep Dive into Decentralized Storage Systems
The digital age has ushered in an era of unprecedented data generation, with individuals, businesses, and institutions producing and consuming vast amounts of information every day. Traditional centra
/images/image1.png)
popular
What is Keccak256? Exploring the Cryptographic Hash Function and Its Use in Cryptocurrencies
Developed as part of the Keccak family of hash functions, Keccak256 was selected as the NIST hash function competition winner and later standardized as SHA-3 (Secure Hash Algorithm 3).
A Brief History
/images/image1.png)
popular
Understanding ECDSA: The Backbone of Digital Signature Security
ECDSA provides secure and efficient signing and verification processes, ensuring data integrity and authentication. This article will explore the fundamentals of ECDSA, its underlying mathematical con
/images/image1.png)
popular
How to Optimize Layer 1 Blockchains for Modularity
One strand of thinking that has become popular in crypto land recently is that the only way for blockchains to solve the Scalability Trilemma—or obtain the trifecta of high security, decentralization,
popular
Secp256k1: A Key Algorithm in Cryptocurrencies
The curve is defined by the Standards for Efficient Cryptography Group (SECG) and represents a specific instance of an elliptic curve over a finite field. This article will explore the significance of
/images/image1.png)
popular
Decentralized Identifiers (DIDs): Creating User-Friendly, Secure, and Interoperable Blockchain Identities
DIDs enable decentralized applications and services by providing unique, user-friendly, and secure identifiers. This article will explore two prominent DID solutions built on different blockchain plat
/images/image1.png)
popular
Zero-Knowledge Proofs: An In-Depth Exploration in Cryptography
Cryptography plays a critical role in the world of cryptocurrencies and blockchain technology, providing security, privacy, and integrity to digital transactions. Among the various cryptographic techn
/images/image1.png)
popular
What is Blockchain Interoperability?
Exploring the importance of cross-chain communication in the blockchain ecosystem.
/images/image1.png)
popular
Surprisingly, Secondary Issuance is not Inflationary
Normally, when we analyze the emission model of a coin such as CKB, we usually only consider the theoretical total number of coins issued over time, i.e., the emission curve. However, this does not fu

popular
A Deep Dive Into the Tokenomics of Nervos Network
The unique tokenomics of Nervos have been specially designed to ensure platform sustainability
popular
Modular vs. Monolithic Blockchains: A Comprehensive Comparison
The rapid development of blockchain technology has brought forth a variety of architectural designs, with modular and monolithic blockchains being two of the most prominent. As the industry seeks to a
/images/image1.png)
popular
Where we're going, we don't need Accounts: the Future of Onboarding
In the 14 years since the inception of Bitcoin, blockchain development shifted through multiple stages, each reflecting the evolving needs and challenges faced by the industry at the respective times.

popular
Proof-of-Work vs. Proof-of-Stake: Unraveling the Key Differences
As blockchain technology and cryptocurrencies continue transforming the digital landscape, understanding the core concepts underpinning their operation is crucial. Among these core concepts, consensus
/images/image1.png)
popular
Understanding the Nervos CKB Issuance Model
Bitcoin’s most important value proposition in the economic sphere is its fixed issuance policy, since it is not subject to any change, and at the same time predictable, as long as we know how much and

popular
Common Knowledge Base (CKB): a Blockchain Developer’s Dream
Any prospective blockchain developer that has tried building decentralized applications has quickly realized that the current blockchains offer rather inflexible development environments. Building app
popular
Pi400 Ubuntu Node Setup Guide
How to run a CKB node on a RaspberryPi 400 with Ubuntu desktop 22.04
Running a node on a RaspberryPi can be a fun, efficient way of helping to decentralise the Nervos Network. Old pro's have probably

popular
Sidechains: Unlocking the Potential of Blockchain Scalability and Interoperability
As the world of blockchain technology continues to expand, sidechains emerge as a promising solution to address some of the limitations inherent in traditional blockchain networks. This article delves

popular
Nervos DAO — Withdrawal Process Explained
To understand how Nervos DAO works, you must first know that it works through cycles, and that each of these cycles are 180 epochs. On the Nervos network, each epoch has an estimated time of 4 hours.

popular
Quantum Resistance in Blockchains: Preparing for a Post-Quantum Computing World
As the field of quantum computing rapidly advances, concerns are growing about the potential impact of these powerful machines on the security of blockchain networks. Quantum computers, with their abi

popular
ASIC-Resistance, is it possible?
ASIC-Resistance describes the ability of a blockchain's mining algorithm to resist implementation of specialized hardware called ASICs (Application-Specific Integrated Circuits). ASICs are specificall

pow
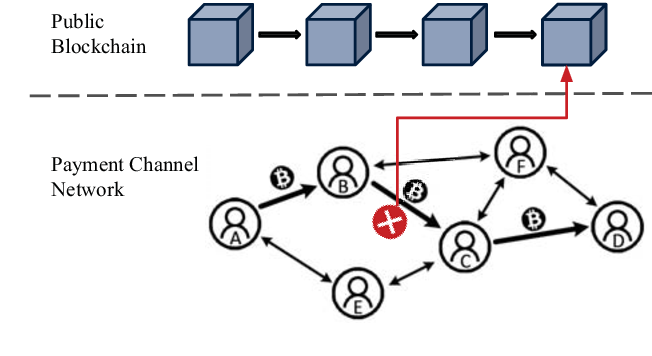
What are Payment Channels?
Payment channels are a unique solution to the scalability problems decentralized blockchains face; they allow for faster and more efficient transactions.
What are Payment Channels?
Payment channels ar
popular
Blockchain Trilemma: The Ultimate Guide
What is the Blockchain Trilemma?
The Blockchain Trilemma is a theory, proposed by Ethereum founder Vitalik Buterin, stating that blockchain networks can’t be secure, decentralized, and scalable all a

popular
What Is a Hash Function?
What Is a Hash Function?
Hash functions are mathematical functions that take an input of any length and transform it into a fixed-length character string. They’re a staple encryption tool in cryptogr

popular

